
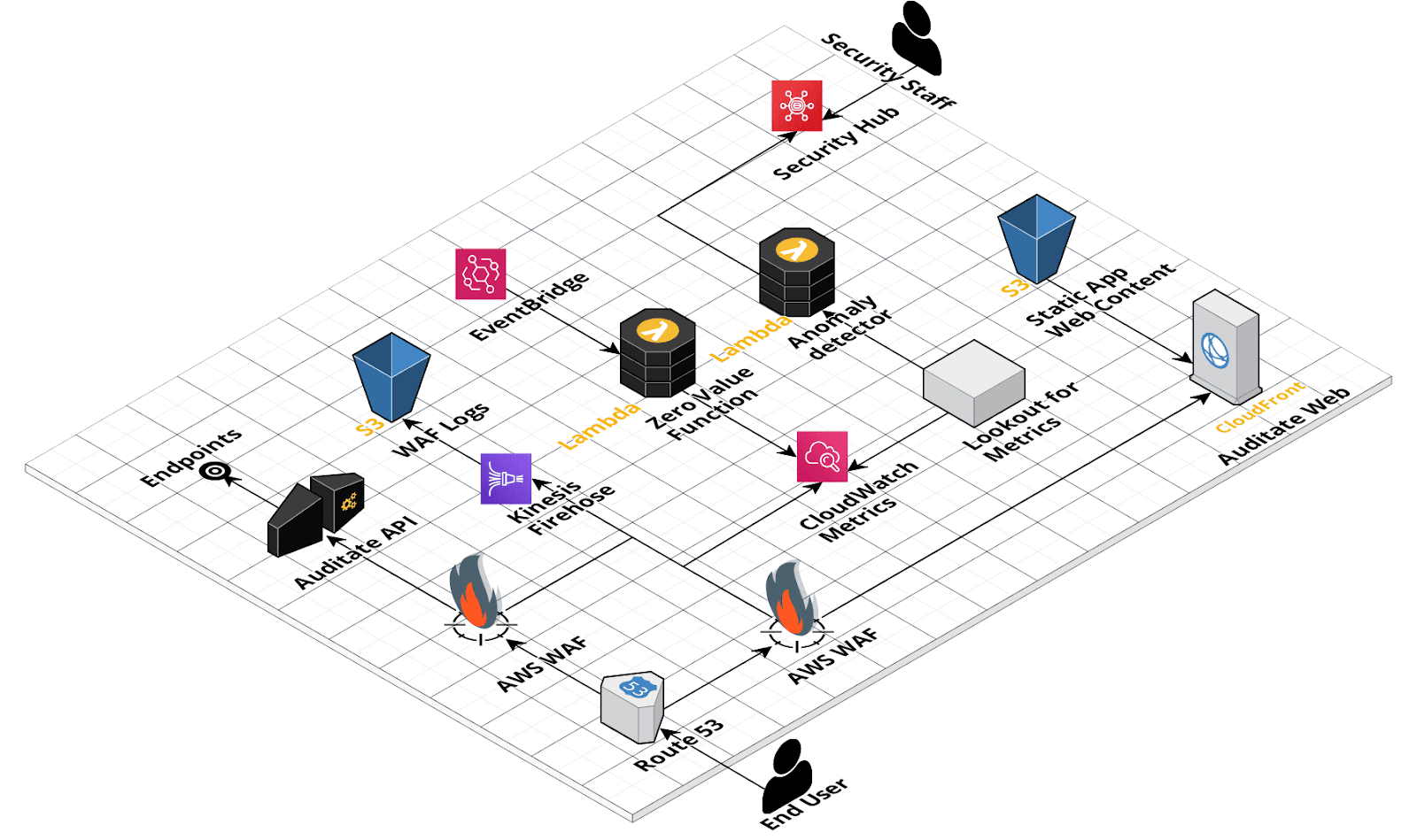
CBQA helped Auditate Inc. add an extra security layer to its Web platform using the AWS native WAF. Additionally, other AWS services were enabled to increase threats visibility and save requests processing activity, creating enough historic data for troubleshooting and security analysis. This information allows us to evaluate the security strategy and make changes to the filtering rules.
Nowadays, Information Systems are the target of many security threats, especially when exposed to the Internet. Connecting Information Systems to the internet poses a serious risk because it opens them up to attacks from anywhere in the world that can occur at any time.. This puts companies at risk because other important assets can be stolen, damaged, or put offline. Therefore, Auditate's Web platform needed a security mechanism that checks Web requests, detects any malicious patterns, blocks dangerous requests, and sends alerts to the organization. In traditional on-premise environments, deploying this kind of security mechanism involves a complicated process that requires a significant amount of time, effort, and money. Throughout this deployment process, on-premise environments are at a higher risk of data breaches, ransomware, DDoS attacks, and so on.
Based on this scenario, we used the AWS Web Application Firewall (WAF) to create Web Access Control Lists (Web ACLs) that control the traffic to the Auditate Web Platform. This was an easy and quick process since WAF is an AWS-managed service allowing us to forgo the provision and management of infrastructure. The Web ACLs contain rules or groups of rules that allow or block requests based on conditions that are configurable. There are some rules that are offered by important security firms such as F5, Fortinet, Imperva ,and so on. On top of these rules, AWS also offers some published group rules that can be used freely. For our project, we applied the following AWS managed rule groups:
- Amazon IP reputation list: Blocks requests from malicious bots and other threats.
- Core rule set: Protects against common Web threats based on OWASP publications Top 10.
- Known bad inputs: Block requests with malicious patterns that are associated with the process of vulnerability discovery and exploitation.
- SQL database: Protects against SQL injection and related threats.
Geomatch rules were also used to block requests based on IP address origin. An IP whitelist was enabled to allow requests from specific origins. These rules were applied to protect the Web Application deployed in Cloudfront and API endpoints deployed in API Gateway to keep the public surface of the Auditate Platform safe.
On threat visibility, we used Cloudwatch metrics to monitor the Web ACL's behavior and identify suspicious activity. We also saved information about the WAF requests process in a safe S3 bucket. This data can be used for security incident investigations and troubleshooting. To keep this information confidential, the bucket is encrypted.
Finally, we deployed an anomaly detection mechanism using Amazon Lookout form metrics.
This mechanism applies ML algorithms to identify patterns and deviations of blocked requests on Cloudwatch metrics.
This service sends alerts to the Security Hub using a Lambda function. In the Security Hub Dashboard, we can view
consolidated information about security findings so we can make informed decisions on remediation security activities.
This project was deployed using Cloudformation and CDK. Both of these AWS technologies help automatize resource provisioning and deployment by utilizing the pattern Infrastructure as Code.
AWS services help us to easily protect our Web Applications and other Information Systems against common security threats.